10 Essential Regulatory Compliance Tips Every Business Owner Must Know
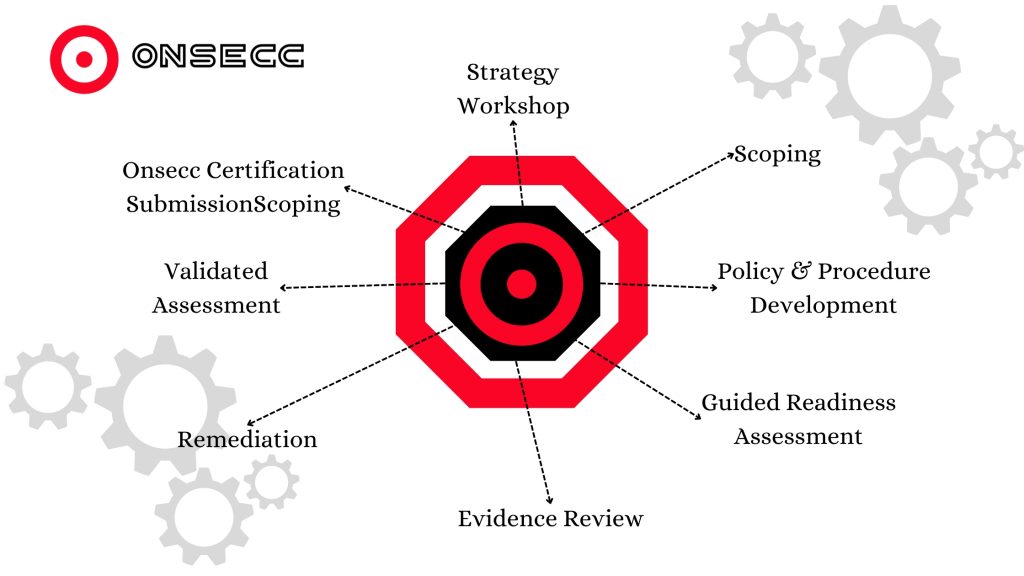
10 Essential Regulatory Compliance Tips Every Business Owner Must Know Regulatory compliance is a critical aspect for businesses, ensuring that operations align with laws, regulations, and standards set by governing bodies. Navigating these requirements can be challenging, but it is essential for maintaining business integrity and avoiding severe penalties. In This Article: Introduction Understanding Regulatory Compliance Benefits of Compliance Conclusion Incorporating statistics and data Free Assessment Introduction Regulatory compliance refers to an organization’s adherence to laws, regulations, guidelines, and specifications relevant to its business operations. Compliance ensures that companies operate within the legal framework and uphold standards set by regulatory bodies. The importance of regulatory compliance spans across various industries, from healthcare and finance to technology and manufacturing. Non-compliance can lead to severe consequences, including legal penalties, financial losses, and reputational damage. This article covers ten essential tips every business owner must know to navigate the complex landscape of regulatory compliance effectively. Understanding Regulatory Compliance Regulatory compliance involves understanding and adhering to a set of regulations and standards applicable to a business. These regulations are designed to protect public interest, ensure fair practices, and maintain ethical standards within industries. Importance of Compliance Compliance is crucial for maintaining operational efficiency and public trust. It ensures that businesses operate within legal boundaries and uphold ethical standards. Compliance also helps in avoiding legal penalties and financial repercussions. Common Compliance Challenges Businesses often face challenges such as understanding complex regulations, keeping up with regulatory changes, and implementing effective compliance management systems. These challenges can hinder compliance efforts and increase the risk of non-compliance. Benefits of Compliance Adhering to compliance regulations offers several benefits, including legal protection, enhanced reputation, operational efficiency, and trust with customers and stakeholders. Compliance also minimizes risks and helps in maintaining a competitive edge. 1. Understand the Specific Regulations for Your Industry Understanding the regulations specific to your industry is the first step towards compliance. Each industry has unique regulatory requirements, and it’s crucial to identify and understand them thoroughly. Identify relevant regulations (e.g., GDPR for data protection, HIPAA for healthcare) Determine specific requirements for compliance Regularly update your knowledge on regulatory changes 2. Implement a Compliance Management System A compliance management system helps in systematically managing compliance efforts. It ensures that all regulatory requirements are met efficiently. Key components of a compliance management system include policies, procedures, and controls Benefits of using compliance management software include automation, efficiency, and accuracy Steps to implement a compliance management system involve planning, execution, monitoring, and continuous improvement Loading… 3. Conduct Regular Compliance Audits Regular audits help in identifying and rectifying compliance issues. They ensure that the business adheres to all regulatory requirements. Importance of compliance audits: they identify gaps and areas for improvement Steps to conduct an effective compliance audit: planning, execution, reporting, and follow-up Frequency of audits: regular intervals, typically annually or semi-annually, depending on industry requirements 4. Train Employees on Compliance Requirements Employee training ensures that everyone is aware of compliance requirements. A well-informed workforce is crucial for maintaining compliance. Topics to cover in training sessions: regulatory requirements, company policies, and procedures Methods of delivering training: in-person sessions, online courses, and workshops Assessing the effectiveness of training: through quizzes, feedback, and performance assessments 5. Develop Clear Compliance Policies and Procedures Clear policies and procedures provide a framework for maintaining compliance. They guide employees on how to comply with regulatory requirements. Essential elements of compliance policies: purpose, scope, responsibilities, and procedures How to document procedures effectively: use clear and concise language, including step-by-step instructions Ensuring policies are accessible to all employees: through an internal portal or manual 6. Monitor and Report Compliance Activities Continuous monitoring and reporting help in maintaining compliance. They ensure that all activities are aligned with regulatory requirements. Tools and techniques for monitoring compliance: software solutions, regular checks, and audits Importance of reporting in compliance management: transparency and accountability Key metrics to track: compliance rates, incidents, and corrective actions 7. Engage with Regulatory Experts Engaging with experts can provide valuable insights and guidance. They help in understanding complex regulations and implementing effective compliance strategies. Benefits of consulting with regulatory experts: expertise, experience, and up-to-date knowledge Types of regulatory experts to engage: consultants, legal advisors, and industry specialists How to choose the right expert for your business: based on their experience, reputation, and alignment with your business needs 8. Implement Strong Data Protection Measures Data protection is a crucial aspect of regulatory compliance. Protecting sensitive information is essential for maintaining trust and avoiding legal issues. Best practices for data protection: encryption, access controls, and regular backups Tools and technologies for data security: firewalls, antivirus software, and intrusion detection systems Legal implications of data breaches: financial penalties, legal action, and reputational damage 9. Stay Updated on Regulatory Changes Regulations are constantly evolving, so staying updated is essential. Keeping abreast of changes ensures that your compliance program remains effective. Sources of regulatory updates: government websites, industry associations, and regulatory bodies How to integrate updates into your compliance program: review and revise policies, train employees, and update compliance management systems Importance of proactive compliance management: it helps in anticipating and preparing for regulatory changes 10. Conduct Risk Assessments Regularly Risk assessments help in identifying potential compliance issues. They ensure that risks are managed proactively and effectively. Steps to conduct a risk assessment: identify risks, analyze their impact, and develop mitigation strategies Tools for risk assessment: risk assessment software, checklists, and templates How to mitigate identified risks: implement controls, monitor their effectiveness, and review regularly Conclusion Regulatory compliance is essential for every business, ensuring that operations align with laws and standards set by regulatory bodies. By understanding specific regulations, implementing a compliance management system, conducting regular audits, training employees, and staying updated on regulatory changes, businesses can maintain compliance effectively. Proactive compliance management not only helps in avoiding legal penalties but also enhances operational efficiency and public trust. Incorporating statistics and data: According to a recent study, businesses that maintain strong compliance programs reduce their risk of regulatory fines by up to 50%.