The Middle East’s Cybersecurity Gap: Building Defenses for a Digital Future
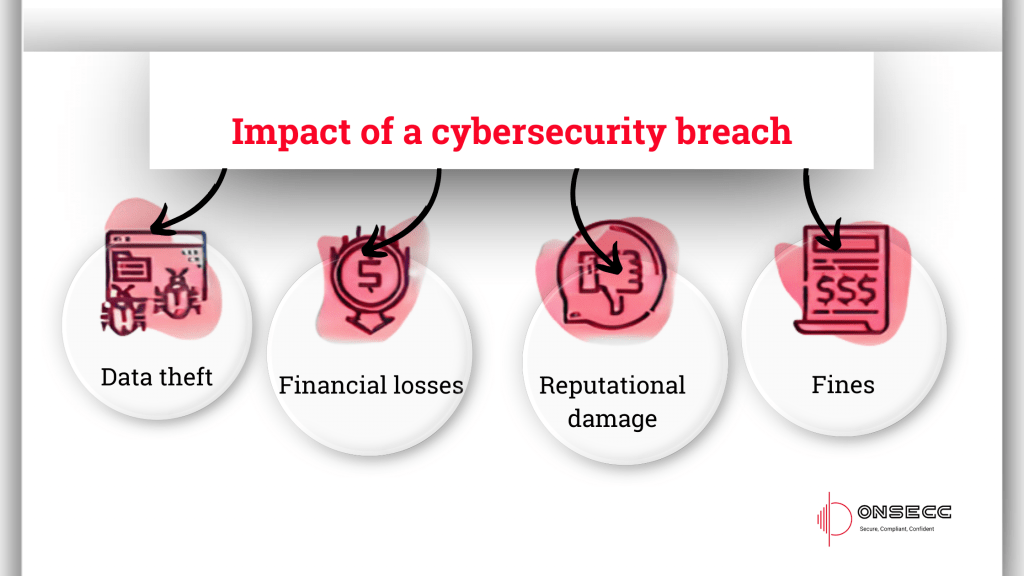
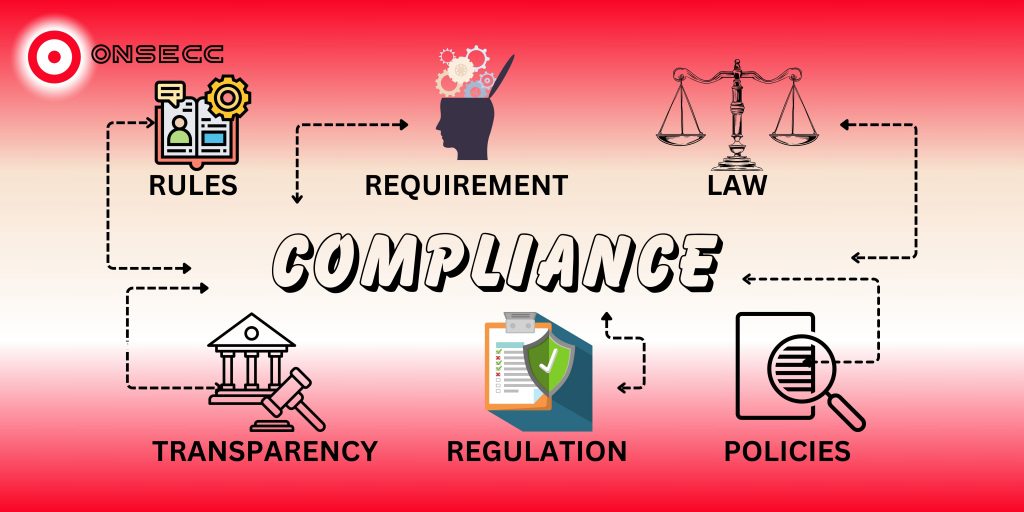
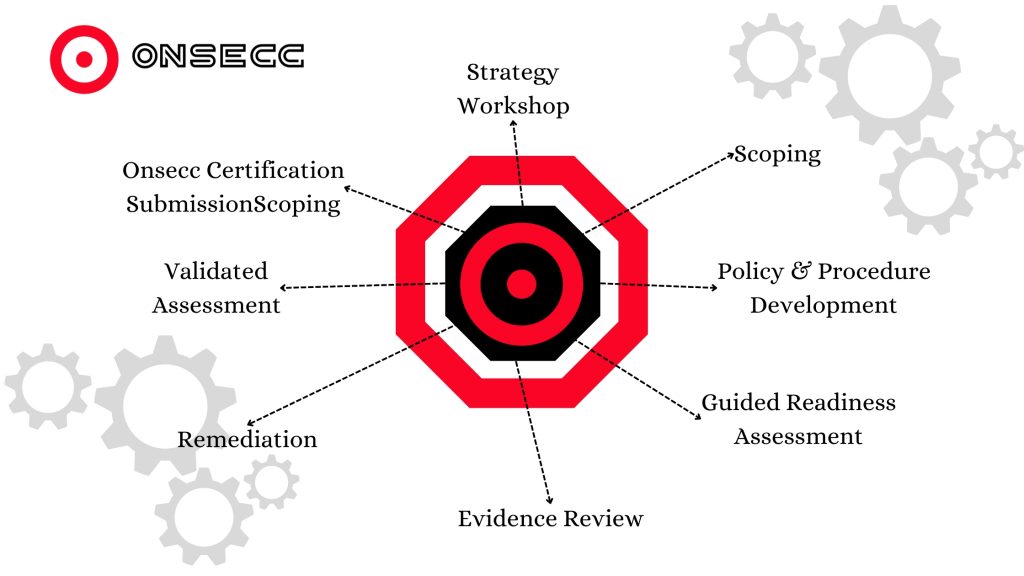
The Middle East’s Cybersecurity Gap: Building Defenses for a Digital Future The Middle East is witnessing a digital transformation at an unprecedented pace. Cities like Dubai, Riyadh, and Abu Dhabi are positioning themselves as global innovation centers. As technology advances, businesses in the region are reaping the rewards of this growth. However, with progress comes risks—cyber threats are rising rapidly, leaving organizations vulnerable. Free Assessment The Cost of Rapid Growth The increased digitization across the Middle East has created a perfect storm for cyberattacks. The UAE, for instance, experiences approximately 50,000 cyberattacks daily. Each successful attack costs millions, affecting businesses, public institutions, and the economy. Distributed denial-of-service (DDoS) attacks alone have increased by 75% in the last year, targeting critical hubs like the UAE and Saudi Arabia. AI is further complicating the problem. It has enabled attackers to scale their efforts with automated phishing and stealthy malware. Businesses relying solely on outsourced cybersecurity measures are finding themselves ill-equipped to address these evolving threats. Outsourcing often delays responses to threats, creating gaps that cybercriminals exploit. Building Internal Defenses Outsourcing security might seem convenient, but it is not a foolproof solution. Businesses in the Middle East must rethink their approach by focusing on building strong, internal cybersecurity teams. An in-house team offers faster response times, better solutions, and a deeper understanding of specific business needs. Onsecc’s expertise in compliance and cybersecurity solutions helps organizations bridge the gap by providing tools for continuous monitoring, risk management, and audit readiness. With Onsecc, businesses can develop in-house capabilities while gaining the support of advanced technologies. To address the regional skills gap, organizations must prioritize hiring, training, and retaining cybersecurity professionals. A lack of local talent has left companies scrambling to fill key roles. Over half of EMEA businesses have reported cybersecurity breaches linked to insufficient training or expertise. The answer lies in nurturing talent within the region. Investing in Talent Hiring experienced cybersecurity professionals is challenging, especially in regions where the talent pool is limited. To overcome this, businesses must look to graduates and apprentices. Collaborating with universities to create internship and graduate programs can help tap into fresh talent eager to learn. Apprenticeships allow companies to mould candidates to fit their needs, creating a pipeline of skilled professionals. Retention is just as important as recruitment. Competitive salaries, benefits, and opportunities for learning and development play a critical role in keeping employees engaged. Investing in training programs not only helps employees stay updated on new threats but also builds loyalty and trust. Reducing Risks Through Awareness Cybersecurity training shouldn’t be limited to IT teams. Many breaches occur due to simple mistakes by employees, such as clicking on phishing links or mishandling sensitive information. A company-wide training program can significantly reduce human error, reinforcing the first line of defence against attacks. Upskilling staff in cybersecurity awareness ensures everyone in the organization is aligned with best practices. Employees become more cautious, informed, and proactive in identifying potential threats. The Path Forward The rise in cyber threats across the Middle East demands urgent action. Businesses cannot afford to rely solely on third-party solutions. They need to build in-house capabilities, invest in local talent, and focus on continuous learning to stay prepared for future challenges. Onsecc offers a platform that supports businesses in creating resilient cybersecurity strategies, ensuring compliance with global standards like ISO 27001 and GDPR. By leveraging Onsecc’s advanced tools and resources, organizations can enhance their defences while maintaining operational efficiency. The region’s rapid digital growth presents both opportunities and challenges. To remain competitive, businesses must treat cybersecurity as a priority, not an afterthought. By taking a proactive approach, Middle Eastern organizations can secure their place in a digital-first world while protecting their operations from the ever-present threat of cyberattacks. Book A Free Call Contact info 3rd Floor, 86-90 Paul Street, London, EC2A 4NE, UK +44-2034880245 hello@onsecc.com Free Assessment Book A Free Call Meet Author Shubham Pandey Linkedin-in Share Blog On Linkedin-in Google-plus-g Instagram Recent Posts: The Middle East’s Cybersecurity Gap: Building Defenses for a Digital Future The Cost of Non-Compliance: What the TfL Cyber Attack Teaches Us GDPR in the United States: A Do or Die Situation for Businesses Is Your Business PCI Compliance Certified? Don’t Risk It! 12 Ways Onsecc Enhances SaaS Cybersecurity Compliance Practical Insights into Implementing ISO/IEC 27001:2022 Strategies to Enhance Cybersecurity for Business Impact of Cybersecurity Breaches on Compliance Status Take the Next Step – Secure Your Compliance Today Let us guide you through a seamless compliance journey. Reach out to Onsecc today for a personalized consultation. Try it for Free! Stay secure, stay aligned,With Onsecc, peace of mind. Home Contact Us hello@onsecc.com +44-2034880245 Subscribe Now Don’t miss our future updates! Get Subscribed Today! ©2024 Onsecc. All Rights Reserved.