Cyber Insurance for Small Businesses: What You Don’t Know Could Cost You Everything
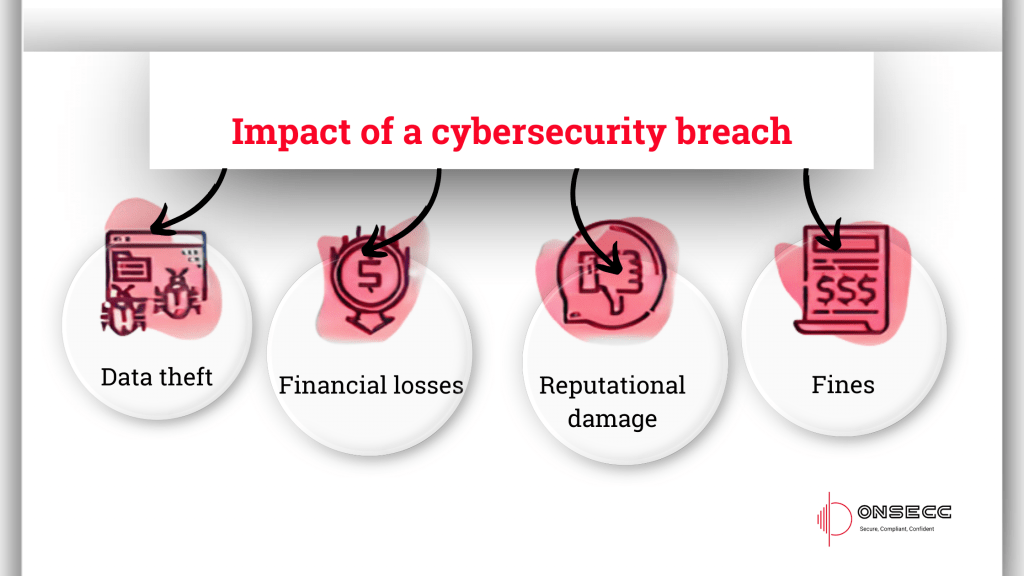
Cyber Insurance for Small Businesses: What You Don’t Know Could Cost You Everything Cyber insurance for small businesses is no longer optional. Today, even the smallest companies are becoming targets for cyberattacks, and insurance is the only thing standing between recovery and collapse. Cyber insurance used to sound like a luxury. In 2025, it’s a life jacket. In This Article What is Cyber Insurance, and Why Should You Care Why Are Small Businesses Prime Cyber Targets Cyber Insurance + Onsecc: Better Together Common Missteps That Kill Claims Final Word: Insurance Can’t Replace Action Free Assessment What is Cyber Insurance, and Why Should You Care? Cyber insurance helps cover the financial fallout of data breaches, ransomware, phishing attacks, and business interruptions due to cyber incidents. It’s not a luxury item—it’s how you pay the bills when the breach hits the fan. Covered Events May Include: Legal and regulatory expenses Customer notification and credit monitoring Data restoration and breach investigation Ransomware payments (yes, it’s a thing) What’s NOT Covered? Your IT guy is clicking on “Free iPads.” Negligence due to a lack of basic cybersecurity practices Breaches from unpatched systems Spoiler: Most denials occur because the business has no security measures. That’s where Onsecc makes you look like a genius. Why Are Small Businesses Prime Cyber Targets? Because you’re vulnerable, profitable enough, and often unaware. 43% of cyberattacks target small businesses Only 14% have cyber insurance Average data breach cost for an SMB: $120,000 Cybercrime isn’t just about stealing data—it’s about draining your time, finances, and reputation. Would your clients stay after hearing, “We lost your data bu,t we’re learning from it”? Cyber Insurance + Onsecc: Better Together Onsecc doesn’t sell insurance. But we make it possible for you to get it—at reasonable rates and with fewer headaches. Here’s how we help: We keep your compliance airtight with real-time monitoring We help you stay audit-ready 24/7 Our documentation tools make insurance applications painless If something goes wrong, you have evidence at your fingertips Insurers love it when clients use platforms like Onsecc. It tells them, “This business takes cyber risk seriously.” That often means faster approval and potentially lower premiums. Common Missteps That Kill Claims Let’s play a game: Will your claim be approved? Did you update your antivirus software this year? No? That’s a problem. Is your employee cybersecurity training older than your office coffee machine? Denied. Can you prove you were monitoring threats? If not, you’re paying out-of-pocket. Cyber insurance doesn’t cover negligence. Onsecc helps you dodge that label. Final Word: Insurance Can’t Replace Action Cyber insurance is your financial parachute. But it doesn’t work if you jump without strapping it on properly. Compliance isn’t just paperwork—it’s protection. With Onsecc, small businesses finally have a way to make cyber hygiene affordable, easy, and reliable. Don’t wait for your wake-up call to be spelled in ransomware. → Start your free trial with Onsecc now 📞 +44-2034880245 🌐 www.onsecc.com 📧 hello@onsecc.com Book A Free Call Contact info 3rd Floor, 86-90 Paul Street, London, EC2A 4NE, UK +44-2034880245 hello@onsecc.com Free Assessment Book A Free Call Meet Author Shubham Pandey Linkedin-in Share Blog On Linkedin-in Google-plus-g Instagram Recent Posts: Cyber Insurance for Small Businesses: What You Don't Know Could Cost You Everything Meet AkiraBot: The AI Spam Demon Haunting 420,000 Websites (and Counting) 2,500 Faces of Deceit: The Proliferation of Malicious Truesight.sys Variants Zero-Day Vulnerabilities: The Invisible Threat Redefining Cybersecurity The Middle East’s Cybersecurity Gap: Building Defenses for a Digital Future The Cost of Non-Compliance: What the TfL Cyber Attack Teaches Us GDPR in the United States: A Do or Die Situation for Businesses Is Your Business PCI Compliance Certified? Don’t Risk It! Take the Next Step – Secure Your Compliance Today Let us guide you through a seamless compliance journey. Reach out to Onsecc today for a personalized consultation. Try it for Free! Stay secure, stay aligned,With Onsecc, peace of mind. Home Contact Us hello@onsecc.com +44-2034880245 Subscribe Now Don’t miss our future updates! Get Subscribed Today! ©2025 Onsecc. All Rights Reserved.